Kubernetes - Network Policy
Alasta 7 Août 2024 kubernetes kubernetes security network policy
Description : Kubernetes, filtrage des flux dans un cluster
DRAFT
Network Policy
Du fait que les pods sont de nature éphémères, il n’est pas possible de faire du filtrage traditionnel avec un firewall/Security Group/NACL dans un cluster Kubernetes.
Pour palier à cela, Kubernetes permet le filtrage au travers des Network Policy, par défaut elle ne sont pas appliquées (allow all).
Les network policy, permettent de filtrer les flux sortant du pod (Egress) et/ou les flux entrant (Ingress).
Mise en place
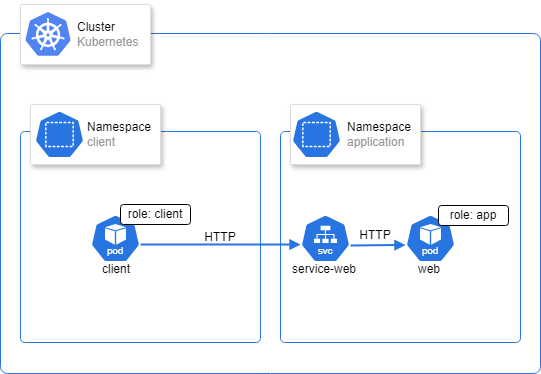
Pour imager cela voici l’architecture Kubernetes.
Configuration de base
Namespaces
apiVersion: v1
kind: Namespace
metadata:
name: client
labels:
name: client
---
apiVersion: v1
kind: Namespace
metadata:
name: application
labels:
name: applicationClient
kind: Deployment
apiVersion: apps/v1
metadata:
name: client-deployment
namespace: client
spec:
replicas: 1
selector:
matchLabels:
app: client-deployment
template:
metadata:
labels:
app: client-deployment
spec:
containers:
- name: client
image: nginx:latestApplication
kind: Deployment
apiVersion: apps/v1
metadata:
name: web
namespace: application
spec:
replicas: 1
selector:
matchLabels:
role: app
template:
metadata:
labels:
role: app
spec:
containers:
- name: web
image: nginx:latest
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: service-web
namespace: application
spec:
type: ClusterIP
selector:
role: app
ports:
- port: 80
targetPort: 80
name: httpTests de connectivités de base
k exec -it -n client client-deployment-ooooooo-xxxxxx -- bash
root@client-deployment-66644bd79c-xgth5:/# curl http://service-web.application.svc
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>Règles par défaut
Par défaut il faut bloquer tout puis autoriser ce qui est necessaire.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-any
namespace: client
spec:
podSelector: {}
policyTypes:
- Egress
- Ingress
ingress:
- from:
- podSelector: {}
egress:
- to:
- podSelector: {}
---
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-any
namespace: application
spec:
podSelector: {}
policyTypes:
- Egress
- Ingress
ingress:
- from:
- podSelector: {}
egress:
- to:
- podSelector: {}Flux applicatif
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: egress-http
namespace: client
spec:
podSelector:
matchLabels:
role: client
policyTypes:
- Egress
egress:
- to:
- podSelector:
matchLabels:
role: app
ports:
- protocol: TCP
port: 80 apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: egress-http
namespace: application
spec:
podSelector:
matchLabels:
role: app
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
role: client
ports:
- protocol: TCP
port: 80